AWS
The AWS bundle installs a catalog scraper that:
- Scrapes AWS Resources and detects changes in the resource definition
- Ingests changes from CloudTrail
- Ingests cost data from AWS Cost & Usage Reporting
- Links AWS EKS resources to the corresponding Kubernetes resources
Prerequisites
- IAM Role for scraping AWS API's
- Mission Control configured to use Pod Identity/IRSA or an AWS access key
Setup
helm repo add flanksource https://flanksource.github.io/charts
helm repo update
helm install mission-control-aws flanksource/mission-control-aws
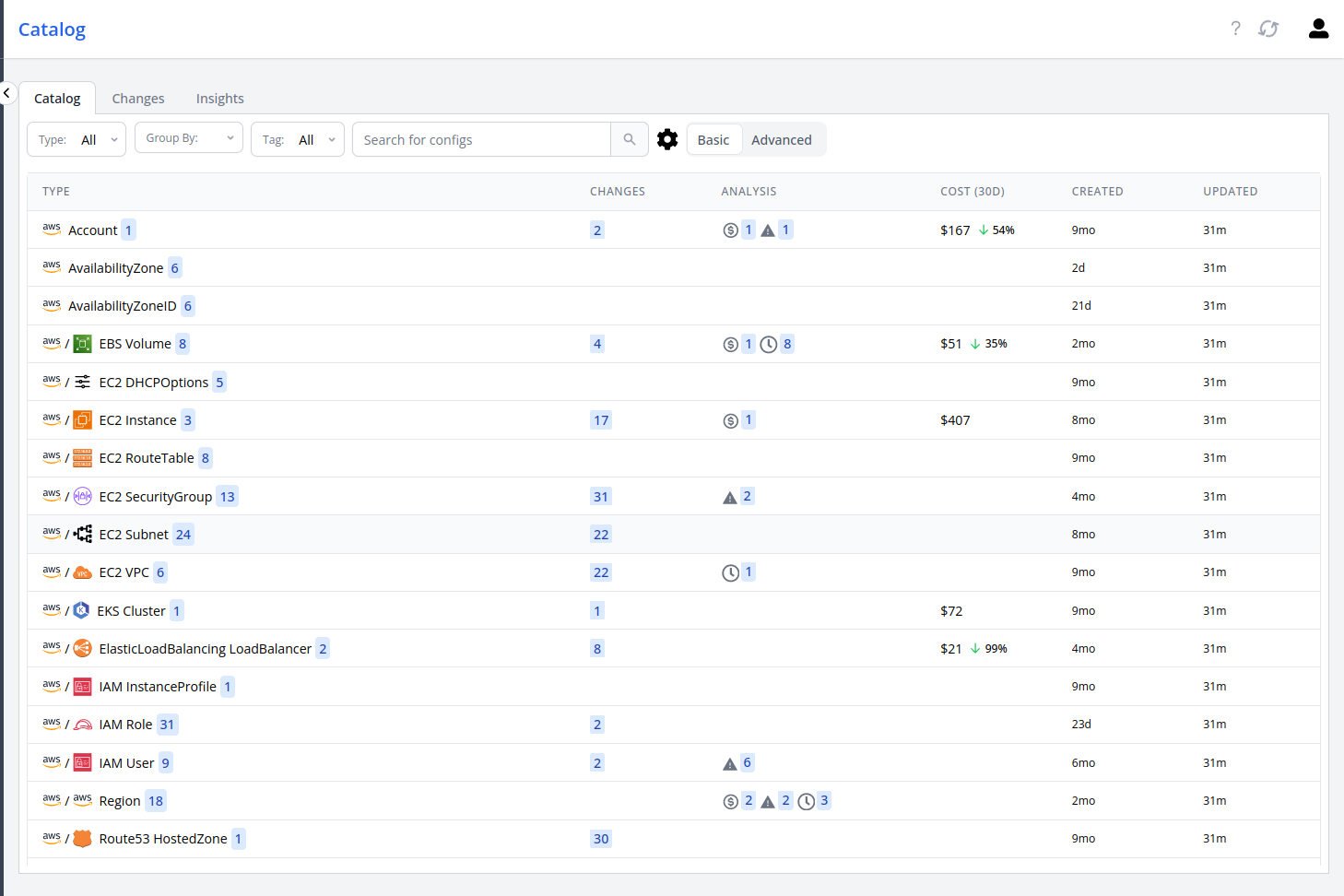
When you go to the catalog now, you can now see all the AWS Resources
Create a role to allow mission-control to scrape your AWS resources. Attach the following AWS managed policies to the role:
ReadOnlyAccessAWSConfigUserAccessAWSQuicksightAthenaAccess
Create new IAM Policy (Alternative)
iam-policy.json{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "mission-control-config-role",
"Effect": "Allow",
"Action": [
"acm:Describe*",
"acm:Get*",
"acm:List*",
"cloudtrail:LookupEvents",
"config:BatchGetAggregateResourceConfig",
"config:BatchGetResourceConfig",
"config:Describe*",
"config:Get*",
"config:List*",
"config:SelectAggregateResourceConfig",
"config:SelectResourceConfig",
"ec2:Describe*",
"ecr:Describe*",
"eks:Describe*",
"eks:ListClusters",
"elasticfilesystem:Describe*",
"elasticloadbalancing:Describe*",
"guardduty:Describe*",
"guardduty:Get*",
"guardduty:List*",
"iam:GetAccountName",
"iam:GetAccountSummary",
"iam:GetGroup",
"iam:GetGroupPolicy",
"iam:GetInstanceProfile",
"iam:GetLoginProfile",
"iam:GetPolicy",
"iam:GetRole",
"iam:GetRolePolicy",
"iam:GetUser",
"iam:List*",
"lambda:List*",
"rds:Describe*",
"sts:GetCallerIdentity"
"trustedadvisor:Describe*",
"trustedadvisor:DownloadRisk",
"trustedadvisor:Get*",
"trustedadvisor:List*",
],
"Resource": "*"
}
]
}
- IAM Roles for Service Accounts
- Pod Identity
a) Get the OIDC ID from your EKS Cluster in the Overview page:

b) Update the trust policy of the IAM role by changing the OIDC arn, OIDC endpoint and the namespace below.
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Principal": {
"Federated":
"arn:aws:iam::<AWS Account ID>:oidc-provider/oidc.eks.us-east-1.amazonaws.com/id/<Your OIDC ID>"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"oidc.eks.<Region>:amazonaws.com/id/<Your OIDC ID>:sub": "system:serviceaccount:mission-control:config-db-sa",
"oidc.eks.<Region>.amazonaws.com/id/<Your OIDC ID>:sub": "system:serviceaccount:mission-control:mission-control-sa",
"oidc.eks.<Region>.amazonaws.com/id/<Your OIDC ID>:sub": "system:serviceaccount:mission-control:canary-checker-sa",
"oidc.eks.<Region>.amazonaws.com/id/<Your OIDC ID>:sub": "sts.amazonaws.com",
}
}
}]
}
Prerequisites
- Pod Identity Agent is installed and configured
a) Modify the trust policy of the IAM role
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowEksAuthToAssumeRoleForPodIdentity",
"Effect": "Allow",
"Principal": {
"Service": "pods.eks.amazonaws.com"
},
"Action": [
"sts:AssumeRole",
"sts:TagSession"
]
}
]
}
b) Create the Pod Identity Association
for role in mission-control-sa canary-checker-sa config-db-sa; do
echo aws eks create-pod-identity-association \
--cluster-name <CLUSTER_NAME> \
--namespace mission-control \
--service-account $role \
--role-arn <IAM_ROLE_ARN>
done
Update the values.yaml to annotate the service accounts:
values.yaml# service account used by for scraping
config-db:
serviceAccount:
annotations:
eks.amazonaws.com/role-arn: <IAM Role ARN>
# service account used by for health checks
canary-checker:
serviceAccount:
annotations:
eks.amazonaws.com/role-arn: <IAM Role ARN>
# service account used for notifications and playbooks
serviceAccount:
annotations:
eks.amazonaws.com/role-arn: <IAM Role ARN>
values.yaml
The following table lists the configurable parameters and their default values:
| Parameter | Description | Default |
|---|---|---|
labels | Additional labels to apply to resources. | |
scraper.name | Name of the AWS scraper. | "aws" |
| Parameter | Description | Schema | Default |
|---|---|---|---|
connectionDetails.connection | AWS connection details. | Connection | "" |
connectionDetails.accessKey | Name of the access key. | EnvVar | "" |
connectionDetails.secretKey | Name of the secret key. | EnvVar | "" |
connectionDetails.region | AWS region. | string | "" |
connectionDetails.endpoint | AWS endpoint. | string | "" |
connectionDetails.skipTLSVerify | Skip TLS verification. | bool | false |
connectionDetails.assumeRole | Assume AWS role. | string | "" |
cloudtrail.maxAge | Maximum age for CloudTrail. | "" | |
cloudtrail.exclude | List of excluded items for CloudTrail. | [] | |
compliance | Enable or disable compliance. | true | |
costReporting.enabled | Enable or disable cost reporting. | false | |
costReporting.database | Cost reporting database. | "" | |
costReporting.region | Cost reporting region. | "" | |
costReporting.s3BucketPath | S3 bucket path for cost reporting. | "" | |
costReporting.table | Table for cost reporting. | "" | |
| regions | |||
includeResources | List of resources to include. | [] | |
excludeResources | List of resources to exclude. | [] |
Prerequisites
- Cost and Usage Reports are configured with an Athena table
- The
AWSQuicksightAthenaAccesspolicy or similar is attached to config-db IAM role